Hello Everyone, Good to see you back, Today's topic is Remote Desktop Connection and I Promise you will become like Pro once you read this carefully.
Before going to direct how to use Remote Desktop first of all we will see everything about Remote Desktop Like It's History, Why use it everything will see one by one.
What is Remote Desktop Connection?
A remote desktop application is a software tool that allows a user to connect to and control a computer or server from a remote location. With a remote desktop application, you can access and control a computer or server from anywhere in the world, as long as you have an internet connection.
The remote desktop application typically consists of two components: a client application that runs on the local computer or device and a server application that runs on the remote computer or server. The client application connects to the server application over the internet and allows the user to view and control the remote computer's desktop as if they were sitting in front of it.
History of Remote Desktop Connection?
The history of remote desktop connection dates back to the early 1990s, when Microsoft introduced the Remote Desktop Protocol (RDP) as part of their Windows NT 4.0 operating system. RDP was designed to allow users to remotely access and control another computer over a network connection.
The first version of RDP, released in 1996, was limited in its capabilities and required significant bandwidth to transmit data over the network. However, subsequent versions of RDP introduced improvements in performance and functionality, including support for multimedia and bi-directional audio.
In 2001, Microsoft introduced Remote Desktop Connection (RDC), a client software that allows users to connect to remote computers running Windows operating systems. RDC replaced the previous remote desktop client, Terminal Services Client (TSC), and introduced several new features, including support for multiple monitors, clipboard redirection, and printing.
Over the years, Microsoft has continued to improve and refine RDP and RDC, with the most recent version of RDP, RDP 10, released in 2018. RDP is now widely used in corporate environments for remote support, remote work, and collaboration.
In addition to Microsoft's RDP, there are also other remote desktop connection protocols and applications available, including VNC, TeamViewer, and AnyDesk. However, RDP remains a popular and widely-used option for remote desktop connection due to its integration with the Windows operating system and its robust security features.
Why we use Remote Desktop Connection?
Remote Desktop Connection is used for a variety of purposes, including:
1. Remote Access: Remote Desktop Connection allows users to access their office or home computer from a remote location, which is useful for employees who work from home or travel frequently. Remote access also enables IT support staff to troubleshoot issues on remote computers without needing to physically visit the computer.
2. Collaboration: Remote Desktop Connection enables multiple users to access and work on a single computer simultaneously, which can be useful for collaborative work and training sessions.
3. File Sharing: Remote Desktop Connection enables users to transfer files between the local and remote computers, which can be useful for sharing documents, photos, and other files.
4. Security: Remote Desktop Connection can be used to securely access and control remote computers, which can be especially important for sensitive applications and data.
5. Flexibility: Remote Desktop Connection provides users with flexibility and convenience, allowing them to access their computer and work from anywhere with an internet connection.
Who can Use Remote Desktop Connection?
Remote Desktop Connection can be used by anyone who needs to remotely access and control a computer over a network or the internet. Some of the common use cases for Remote Desktop Connection include:
1. Remote workers: Remote workers can use Remote Desktop Connection to access their office computer from a remote location, allowing them to work from home or other remote locations.
2. IT support staff: IT support staff can use Remote Desktop Connection to remotely troubleshoot and resolve issues on remote computers without needing to physically visit the computer.
3. Collaboration: Remote Desktop Connection enables multiple users to access and work on a single computer simultaneously, which can be useful for collaborative work and training sessions.
4. Students and educators: Remote Desktop Connection can be used in education settings to provide students and educators with remote access to computer resources and applications.
5. Businesses: Remote Desktop Connection can be used by businesses to provide employees with access to remote resources and applications, as well as to facilitate collaboration and remote work.
On Which language Remote Desktop Connection design?
Remote Desktop Connection is a software application developed by Microsoft, and it is primarily designed using the programming languages C++ and C#. C++ is a powerful, high-performance language that is commonly used for system-level programming, while C# is a modern, object-oriented language designed for developing applications on the .NET Framework.

The Remote Desktop Protocol (RDP), which is the protocol used by Remote Desktop Connection to establish a remote connection between two computers, is also designed using C++. RDP is optimized for performance and efficiency, which is critical for providing a seamless remote desktop experience.
How to Use Remote Desktop Connection? Step by Step?
Here We are providing Real time example to access your Remote Desktop Connection application.
these are the steps to use Remote Desktop Connection:
1. Ensure that your computer is set up for remote desktop connections: Before you can use Remote Desktop Connection, you must enable remote connections on your computer. To do this, go to the System settings on your computer and select "Remote Desktop". Ensure that the "Allow remote connections to this computer" option is selected.
2. Obtain the IP address or computer name of the remote computer: To connect to a remote computer, you need to know its IP address or computer name. You can obtain this information from the remote computer's user or IT support staff.
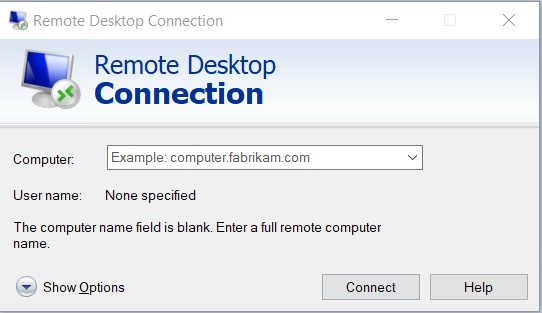
3. Launch the Remote Desktop Connection application: On your local computer, launch the Remote Desktop Connection application. You can typically find this application by searching for "Remote Desktop Connection" in the Start menu.
4. Enter the IP address or computer name of the remote computer: In the Remote Desktop Connection window, enter the IP address or computer name of the remote computer that you want to connect to.
5. Enter your credentials: In the Remote Desktop Connection window, enter your username and password for the remote computer. Ensure that you have the appropriate permissions to access the remote computer.
6. Connect to the remote computer: Click the "Connect" button in the Remote Desktop Connection window to connect to the remote computer. If this is your first time connecting to the remote computer, you may need to accept a security warning before the connection is established.
Once you enter correct credentials then at last it will ask to Ok for connection. Please do it Ok and enjoy your Remote connection.
7. Use the remote computer: Once the connection is established, you can use the remote computer as if you were sitting in front of it. You can run applications, access files, and perform other tasks on the remote computer.
8. Disconnect from the remote computer: When you are finished using the remote computer, click the "X" button in the Remote Desktop Connection window to disconnect from the remote computer.
What are Benefits and Drawbacks of Remote Desktop Connection?
Remote Desktop Connection has several benefits and drawbacks, which are listed below:
Benefits:
1. Remote access: Remote Desktop Connection allows users to remotely access and control another computer over the internet or a local network, which can be helpful in a variety of situations.
2. Increased productivity: Remote Desktop Connection can increase productivity by allowing users to access and work on their computers from anywhere, at any time.
3. Cost savings: Remote Desktop Connection can reduce costs by eliminating the need for physical travel to remote locations and by enabling remote IT support.
4. Centralized management: Remote Desktop Connection can simplify IT management by allowing IT administrators to manage multiple computers and users from a single location.
5. Enhanced security: Remote Desktop Connection can improve security by allowing users to access their computers remotely without the need for physical access, which can reduce the risk of theft, loss, or damage to the computer.
Drawbacks:
1. Security risks: Remote Desktop Connection can pose security risks if not properly secured, including the risk of unauthorized access and data breaches.
2. Performance issues: Remote Desktop Connection performance can be affected by factors such as network latency, bandwidth limitations, and the performance of the remote computer.
3. Compatibility issues: Remote Desktop Connection may not be compatible with all applications or operating systems, which can limit its usefulness in certain situations.
4. Network reliability: Remote Desktop Connection relies on network connectivity, which can be affected by factors such as network outages, congestion, and bandwidth limitations.
5. User error: Remote Desktop Connection can be affected by user error, such as misconfigured settings or incorrect credentials, which can result in connection issues or security vulnerabilities.
How Does Remote Desktop Connection Work?
Remote Desktop Connection works by allowing a user to connect to and control another computer remotely over a network connection. The connection is made using the Remote Desktop Protocol (RDP), which is built into Windows operating systems.
Here is a step-by-step explanation of how Remote Desktop Connection works:
1. Enable Remote Desktop on the remote computer: The user must first enable Remote Desktop on the computer that they want to connect to. This can be done by going to the System Properties in the Control Panel and selecting the Remote tab.
2. Connect to the remote computer: The user can then connect to the remote computer using Remote Desktop Connection, which is built into Windows. They will need to enter the IP address or hostname of the remote computer and their login credentials.
3. Authentication: Once connected, the user's credentials will be authenticated, and they will be granted access to the remote computer.
4. Remote control: The user can then remotely control the remote computer, including accessing files, running applications, and performing other tasks as if they were physically sitting in front of the computer.
5. Terminate the connection: Once the user is done working on the remote computer, they can terminate the connection using Remote Desktop Connection.
Remote Desktop Connection uses encryption to secure the connection between the two computers, and the remote computer can be accessed from anywhere over a network connection. It is important to ensure that the remote computer is properly secured, and that Remote Desktop is only enabled for authorized users.
Which are list of application like Remote Desktop Connection?
There are several applications like Remote Desktop Connection that allow users to remotely access and control other computers. Some of the popular alternatives include:
1. TeamViewer: TeamViewer is a remote access and support software that allows users to connect to and control other computers over the internet.
2. VNC Connect: VNC Connect is a remote access software that allows users to access and control other computers over the internet.
3. AnyDesk: AnyDesk is a remote desktop software that allows users to access and control other computers over the internet.
4. LogMeIn: LogMeIn is a remote access software that allows users to access and control other computers over the internet.
5. Chrome Remote Desktop: Chrome Remote Desktop is a web-based remote desktop software that allows users to access and control other computers through a web browser.
Thanks for Reading this useful information. Keep with us for new upcoming useful real time IT(Software) Industry tools posts.
































